How to Login to Linux Server Using Putty
This page is about the PuTTY SSH client on Windows. For information about PuTTY on Mac, see the PuTTY Mac page. For PuTTY on Linux, see the PuTTY Linux page. This page explains how to use the PuTTY terminal window on Windows. How to configure PuTTY, how to create and save profiles, and what configuration options to change. Advanced topics, such as configuring public key authentication, are also addressed. You can download a copy of the software for the Windows platform from the download page. Detailed installation instructions are provided on the installation instructions page. If you selected to create a desktop icon during installation, you can start the software simply by (double-)clicking on the icon. Otherwise, open the software from the Windows Start menu. When the software starts, a window titled PuTTY Configuration should open. This window has a configuration pane on the left, a Host Name (or IP address) field and other options in the middle, and a pane for saving session profiles in the lower right area. For simple use, all you need to do is to enter the domain name or IP address of the host you want to connect to in the Host Name field and click Open (or press Enter). A domain name looks like If you don't have a server to connect to, you can try Tectia SSH on Windows or OpenSSH on Linux. When you connect to a server for the first time, you are likely to see a But as said, the first time you connect, this is normal, and you should just click Yes. If you want to be fancy, you can check the displayed key fingerprint and make sure it is the same that is used by the server. In real life, almost nobody does that. It is more secure to use a proper SSH key management solution anyway. After the security alert, you should get a terminal window. By default, this is a black, very bland window. It should first ask for your user name and then password. After these, you should get a command line on the server. You can then type into the terminal Window. You are now connected to the server, and anything you type in the Window is sent to the server. Server's responses are displayed in the Window. You can run any text-based applications on the server using the window. The session terminates when you exit the command-line shell on the server (typically by typing The initial configuration window contains a lot of options. Most of them are not needed in normal use. The port field specifies the TCP/IP port to connect. For SSH, this is the port on which the SSH server runs. Normally it can be left to 22. If for some reason you need to connect to a different port number, just change the value. Usually only developers would change this to a different value, but some enterprises are known to run SSH servers in non-standard ports or to run multiple SSH servers on the same server at different ports. The Connection type selection almost never needs to be touched. Just leave it as SSH. SSH is a secure, encrypted communications protocol designed to ensure your password and data are maximally protected. Raw connections might be used for developers to connect a TCP/IP socket for testing (e.g., when developing a network application that listens on a TCP/IP port). Telnet is an old legacy protocol that is almost never used, unless you manage equipment that is more than 10 years old. Telnet is not secure. Passwords are sent in the clear on the network. Attackers can easily eavesdrop on plaintext communications and steal user names and passwords. Rlogin is another legacy protocol with similar woes. Serial refers to a serial port, another legacy communications mechanism for connecting computers to peripheral devices. Most PCs these days no longer have serial ports, but they are still sometimes used for controlling physical equipment, instrumentation, machinery, or communications devices. Another use for serial ports is debugging operating systems or embedded software. This section allows you to save your settings as named profiles. Just write the name of your new profile in the Saved Sessions box and click Save to create a new profile. The host name and your other settings are saved in the profile. Saved profiles appear in the larger box below it. Initially it will contain just Default Settings. Profiles you save will be included there. Select a profile and click Load to use a previously saved profile. Select a profile and click Delete to delete a profile that is no longer needed. Finally, the Close window on exit setting specifies whether the terminal window should be automatically closed when the connection is terminated. There is rarely any need to change it from the default value of Only on clean exit. More options can be found in the left pane titled Category. Select a category from the tree, and the right pane will change to show configuration options for that category. The initally shown options belong to the Session category. Only the more relevant options are described here. There are lots of options, and most of them would never be used. The options in this category influence terminal emulation and keyboard mappings. They are largely self-explanatory, and will not be covered here. Very few people need to touch these. Some people may change how the bell character is handled; people using exotic operating systems might change what is sent by the backspace or delete character. The window options influence the appearance and behavior of the terminal window. It can also specify how characters are translated on output and to select fonts and colors for the window. Of the connection options, the Data options can be useful. The Auto-login user name specifies the user to log in as, so that the name will not have to be entered every time. The Proxy options are rarely useful for home users, but may be needed in enterprises that do not allow outgoing Internet connections without using a SOCKS proxy or other similar mechanisms. Don't worry if you don't know what a SOCKS proxy is; just stay out of that section. The Telnet, Rlogin, and Serial categories only contain options for those protocols, and very few people would ever use them. The SSH options, however, are important and useful for some people. The ordinary user or student need not worry about them. But if you want to use public key authentication, then they are needed. Note that you need to open the SSH options subtree by clicking on the small You almost never want to touch the Kex (key exchange), Host Keys, or Cipher options. They all have reasonable default values, and most people don't know enough about cryptography to select any better values. Thus just skip these options, unless you know what you are doing. The Auth subtree contains some options that may be useful. When Auth is clicked, it shows a pane titled Options controlling SSH authentication. To enable public key authentication, you just generate an SSH key and then click the Browse button in the Authentication parameters box in the middle right area of this configuration pane. For more information, see also configuring public key authentication for PuTTY. Advanced users may also want to check the Allow agent forwarding checkbox to use key-based single sign-on. Most users have no need to generate SSH keys and need not know what public key authentication is. System administrators, however, should learn it and should also familiarize themselves with SSH key management and ensure their organization implements proper provisioning and termination processes and audits for SSH keys. One of the interesting features of PuTTY is support for Active Directory single sign-on. Technically it uses the Kerberos protocol via a programming interface called GSSAPI. In the SSH protocol, the mechanism is called GSSAPI authentication. Enterprise users using Kerberos authentication (e.g., via the Centrify or Quest Authentication Services aka Vintela) may want to take advantage of the single-sign-on capability. Other users don't need to care. The settings for GSSAPI authentication can be found under the SSH / Auth section. Note that you must again expand the Auth section by clicking on the X11 is a protocol and system for running graphical applications on Unix and Linux. It supports running graphical applications remotely over a network out-of-the-box. PuTTY does not implement an X11 server (the display side), but it can work with some other product that implements X server functionality on Windows. A popular free alternative is XMing. To use an X11 server, you need to check the Enable X11 forwarding box and enter localhost:0.0 in the X display location box. The other settings need not be touched. Detailed instructions can be found, e.g., here. The final category of configuration options we'll discuss is Tunnels. They are used for configuring SSH tunneling, also called SSH port forwarding. This panel can be used for defining forwardings for the connection. Forwardings are saved in the profile. To add a local forwarding (i.e., TCP/IP port on local machine forwarded to a port on the remote machine or to a machine reachable from the remote machine), write the source port in the Source port field, the destination host and port (e.g., To add a remote forwarding (i.e., a TCP/IP port on the remote machine forwarded to a port on the local machine or to a machine reachable from the local machine), specify Source port on the destination machine and Destination that is reachable from the local machine (your desktop). Normally you need not check Local ports accept connections from other hosts or the same for remote ports. However, if the connection to the forwarded port is from a over a network instead of from Getting and installing
Running PuTTY and connecting to a server
students.example.edu. An IP address looks something like 78.99.129.32.What if you don't have a server
Security alert dialog box
PuTTY Security Alert dialog about the server's host key not being cached in the registry. This is normal when you are connecting to a server for the first time. If you ever get this with a server, it could mean that someone is trying to attack your connection and steal your password using a man-in-the-middle attack.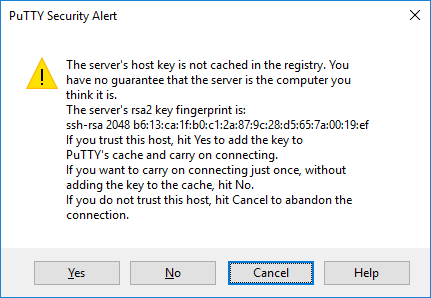
Terminal window and login credentials
exit) to the command line or pressing Control-D. Alternatively, you can forcibly terminate the session by closing the terminal window.
Configuration options and saved profiles
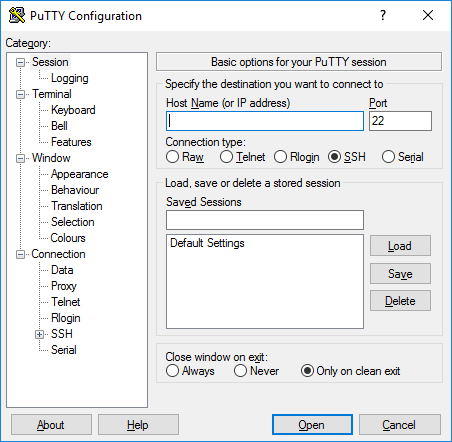
Port
Connection type
Load, save, or delete a stored session
Close window on exit
Left pane configuration options
Terminal options
Window options
Connection options
[+] symbol. Otherwise you won't see all the options.Key exchange, host keys, and cipher options
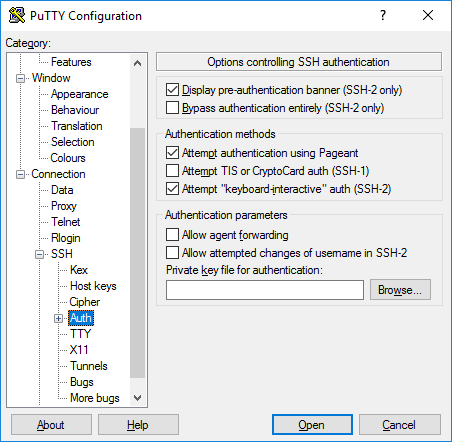
Authentication options - public key authentication
Active Directory authentication (GSSAPI / Kerberos)
[+] symbol to see the GSSAPI options.X11 forwarding options
Tunneling options
www.dest.com:80) in the Destination field, and select Local. The click Add.localhost, then you need to check these. There is a small security risk, but usually it is not a problem in the cases where SSH tunneling is used. However you should understand that anyone who can connect to the respective computer can then connect to the forwarded port. In some cases port forwarding can be used to traverse firewalls. We suggest you read our article on the risks of SSH port forwarding.
How to Login to Linux Server Using Putty
Source: https://www.ssh.com/academy/ssh/putty/windows